Our products are based on a robust composition of well-established IT security technologies and pioneering developments in data science, AI and ML
We take lifecycle approach to every project that we participate in. Starting with consulting services and initial assessments and working through proof-of-concept and pilot projects all the way to overall system design, implementation and commissioning
Flow
Minimize the cyberphysical risks by arming your team with the comprehensive industrial security solution from CyberLympha and ensure operational resilience for OT, IoT and IIoT infrastructures by applying security as a process
Knowing your infrastructure comes first. CyberLympha solutions use multiple types of incoming data to build a comprehensive picture of the protected infrastructure and analyze the security status of its components
No time spared for the adversary to act. Constant analysis of available information covering several aspects of asset security allows a timely and precise security incident detection, enabling security team to deliver prompt countermeasures and minimize possible impact on OT operation
24/7 confidence in OT security. Continuous asset security status monitoring and compliance control based on worldwide-adopted best practices, ICS vendor recommendations and industry standards.
-
Key
IndustriesTrusted by enterprise customers across multiple industries
-
 OIL & GAS
OIL & GAS- Large number of small isolated sites
- Challenging WAN links
-
 Energy & Generation
Energy & Generation- Multiple control systems on every site
- Centralized corporate SOC
-
 Metallurgy
Metallurgy- Extensive resilience requirements due to the tech-process
- Distributed organizational structure
-
 Manufacturing
Manufacturing- Legacy ICS/OT equipment
- Traffic isolation control required
-
 Smart city
Smart city- Numerous PLCs and IoT subsystems
- Single point of infrastructure control
-
 Nuclear Energy
Nuclear Energy- Industry-specific systems and protocols
- Strict security measures
-
 Chemical Industry
Chemical Industry- Limited personnel resources
- Outsourced SOCs
Cybersecurity has firmly taken the headlines in the media worldwide and that happens for a reason. OT segment is slowly becoming a likely target for automated and human-operated attack scenarios. Read our executive brief to learn what steps can your Company take to counter the threats
Read Executive brief
-
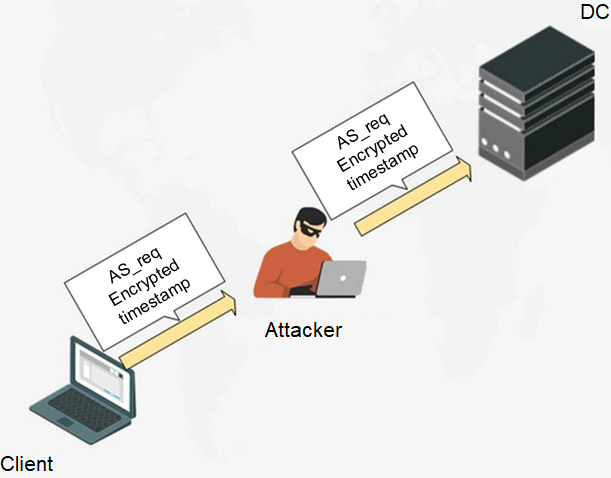 Kerberoasting v218.04.2023
Kerberoasting v218.04.2023 -
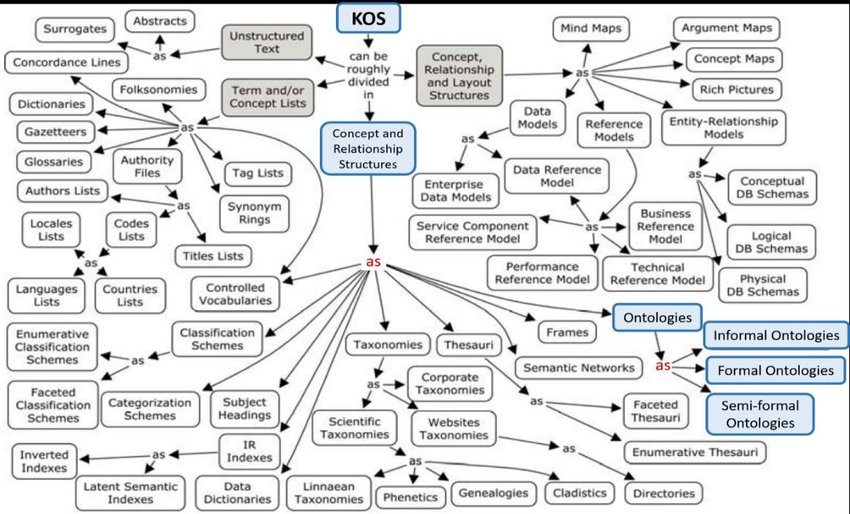 Ontologies (Part 1)09.12.2022
Ontologies (Part 1)09.12.2022 -
 Anomalies Detection in Time Series28.09.2022
Anomalies Detection in Time Series28.09.2022



